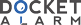`
`Computer and
`
`Internet Terms
`
`Sixth Edition
`
`Douglas A. Downing, Ph.D.
`.S'r1'mn.' nfB:r.s'im’s_\‘ (1!IdE('(?}?0fili(‘.T
`.S'e*(mic’ Ptrvific‘ {/':u'\‘m'.\'fr_\‘
`
`Michael A. Covington. Ph.D.
`f'liT.'7-fi'('l'.'.}l.T .7rlJ£'Hi_§§'(‘fl('(‘ C”t=nrm‘
`The U'ni\'€!‘.ti.')‘
`r2_fGm1'_2r'u
`
`Melody Mauldin Covington
`(‘rlwlvrglvrl 1'mmmrfnm‘
`Arlivm. Gt=r:rj::i:1
`
`§@
`
`BARRON’S
`
`
`
`
`
`CONTENTS
`
`About the Authors
`
`To the Reader
`
`Dictionary
`
`Characters and Symbols
`
`Copyright I993 by BarrnI1‘s‘Ed1icalinn:tI Series. Inc.
`Priur editions © copyright I996, i995. 1992. I989. and 1936
`h_\ Barron‘.~: Educational Series. Inc.
`
`All rights. reserved.
`\'u part ofthis book may be reproduced in any form. by phomslat. microfilm.
`wrography. or any other means. or incorporatctl into any information
`1'c‘lFiI?\.'3ll :ys'l:‘n1.eIectrnnic nr mechanical. without the written pcrrnisvinn
`oi the copyright owner.
`
`All’ mqtt."a'ic'.r sfrzitilrl be cru'cfr':'.s'.s'¢'z.' rrr
`B:1IT0n‘.\' F.duc:1tinnal Series. Inc.
`250 Wireless Boulevard
`Hnuppauge. New York 11788
`http:I/www.l'::irr0nset:luc.t:o1n
`
`t'_rf7mr'_\‘ r>j'CnIrgr‘r’.\‘5 C(r!L1t'()_t1 Cam’ Nu. 93-6984
`International Staindnrd Book
`(J-764]-0094-7
`
`Library of Congress Cataioging-in-Publication Data
`Dnwning. Dougias.
`Dictionary of computer and Internet tertm 1‘ Douglas A, Downing.
`Michael A. (Ttwinglnn. Melody Mztuldin CuvingIon—6th ecl.
`.
`CITI.
`First-4th eds. published undertitle: Dictionary ofcumputer
`tenns.
`ISBN U-764 I -U094-7
`2. Internet (Computer networkl—
`I. Con1putcrs—DicIinnaric.~:.
`Dtcttosiaries.
`1. Covington. Michael A., i957—
`.
`II. Ctwingtou.
`\i:End_\ Mauldin.
`III. Downing. Douglas. Dictionary ufcumputer
`'-.'r'1nx
`I\-", Title.
`Q.-\‘h lS.D6(:7
`1998
`- L2‘ II=—dc2l
`
`9846934
`CIP
`
`"- .\ E El.) i\ THE UNITED STATES OF AMERICA
`
`
`
`7
`
`159
`158
`end
` environment
`using a key given as a binary number. A longer key provides greater
`computer control circuitry. Many laser printers use an engine made by
`Canon in Japan.
`security, but the calculation process becomes more complicated.
`All this presumes that you can get people's public keys reliably so
`that you can be sure you're really using Bob‘s public key when you
`send messages to Bob. Since public keys are not secret. all you need is
`a trustworthy database in which you can look up people's public keys.
`Another issue is that the U.S. Government presently regulates the
`export of strong encryption software in the same way that it regulates
`the export of weapons. This regulation dates from the 1940s. before
`general—purpose digital computers existed: encryption machines at
`that time were considered to be munitions. and they still are. Almost
`everyone in the computer industry wants this outdated regulation to be
`repealed.
`See aim DIGITAL SIGNATURE; DES; POP; RSA ENCRYPTION; SSL;
`ONE-WAY FUNCTION; HASH FUNCTION.
`
`EI:lIAtC _(Electronic Numerical Integrator And Calculator) the first
`ec ronic computer, built at the University of Pennsylvania in the mid-
`1940s. It contained about 13.000 vacuum tubes. Initially the ENIAC
`W35 PTOEF-'=“'1'|lTl€d by plugging cables into circuit boards. Today. one of
`ghe Internet nodes at the University_ol‘ Pennsylvania is named eniac
`ut is. of course, not the same machine.
`
`end
`
`keyword that marks the end of a particular program structure
`1.
`in several programming languages. In BASIC. the END keyword tells
`the computer to stop executing the program. In Pascal, END marks the
`end of blocks of statements that start with BEGIN.
`2.
`the key on your keyboard that takes your cursor to the end of
`the current line. Some word processors use Ctrl-End as a keyboard
`shortcut to take you to the end of the document.
`en dash a short dash (—). See DASH.
`
`end-of-file mark a symbol that indicates the end of a file. For exam-
`ple,
`in CP/M, all text files ended with ASCII character 26 (Ctrl—Z')
`because the computer did not otherwise keep track of the exact length
`of the file. only the number of disk sectors. In DOS. Windows. and
`OS/2. Ctrl-Z is often used the same way even though the computer
`knows exactly where the file ends whether or not an end-of-file mark
`is present. The UNIX end~of-file mark is Ctrl—D.
`end user the person ultimately intended to use a product. as opposed
`to people involved in developing or marketing it.
`
`Energy Star a set of guidelines proposed by the U.S. Environmental
`Protection Agency in 1992 to reduce the amount of electricity con-
`sumed by personal computers. An Energy Star-compliant computer
`consumes less than 30 watts of power when idling (i.e.. when turned
`on but not in use) and switches automatically into low-power mode if
`several minutes elapse without any keyboard activity. See GREEN PC.
`
`engine
`the part of a computer program that implements a special tech-
`1.
`niquc; Set’ INFERENCE ENGINE. MONTE CARLO ENGINE. SEARCH
`ENGINE.
`
`2.
`
`the printing mechanism of a laser printer. not including the
`
`the key on a computer keyboard that you press at the end
`do me in order to send the contents ot that line into the corn.
`PUVEI1 On most keyboards. the Enter key is the same as the Return key.
`HOWEVBII IBM 3270-series terminals make a distinction: the Return
`key 93715 3 NEW “'16. but 1116 Entcl‘ key sends the contents of the whole
`screen to the computer.
`Under Windflwed Gperallng Systems. pressing the Enter key is usu-
`ally equivalent to clicking on the currently selected icon or other high-
`lighted item.
`
`enumerator a device driver or operating system component that iden-
`tifies all hardware devices of a particular type. See 3105 I;-‘_NUMERA_
`TOR.
`'
`
`
`;
`';'p'
`. E ‘L in!
`I .
`.
`.
`.
`.
`
`. .. .
`
`.
`
`.
`
`.
`
`.
`
`'
`‘
`. .-
`
`E
`
`5
`
`FIGURE 85. ENVELOPE MANIPULATION
`
`
`envelope
`1-
`(in -'=_1 draw program) the imaginary outline enclosing an object.
`T1011 C311 Edit the envelope, turning it from a rectangle into ;i curved
`shape. and thereby distorting everything inside it_
`2.
`(in engineering) the limits imposed by physical or tech,-ma]
`constraints (called an “envelope" because they can be envisioned as
`surrounding an area on _a graph). “Pushing the envelope" means work-
`mg close to. or at. the limits.
`environment
`1.
`the display and human interface provided by software On a
`computer. an environment defines what you can do with the computer,