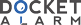`(19) World Intellectual Property
`Organization
`International Bureau
`
`(10) International Publication Number
`
`\Q
`
`(43) International Publication Date
`WO 2014/183059 A1
`13 November 2014 (13.11.2014) WIPOI PCT
`
`
`(51)
`
`International Patent Classification:
`H04L 1/00 (2006.01)
`H04L 27/18 (2006.01)
`
`(21)
`
`International Application Number:
`
`PCT/[1820 1 4/037534
`
`(22)
`
`International Filing Date:
`
`(25)
`
`Filing Language:
`
`(26)
`
`Publication Language:
`
`9 May 2014 (09.05.2014)
`
`English
`
`English
`
`(30)
`
`(71)
`
`(72)
`(71)
`
`(74)
`
`(81)
`
`Priority Data:
`61/821,947
`
`10 May 2013 (10.05.2013)
`
`US
`
`LTD.
`Applicant: MARVELL WORLD TRADE
`[BB/BB]; L' Horizon, Gunsite Road, Brittons Hill, St. Mi-
`chael, BB 14027 (BB).
`
`Inventor; and
`Applicant flor US only): ZHANG, Hongyuan [CN/US];
`4707 Paseo Padre Parkway, Fremont, CA 94555 (US).
`
`Agents: STANTON, Gregory, E. et al.; Drinker Biddle &
`Reath LLP, 191 N. Wacker Drive, Suite 3700, Chicago, IL
`60606—1698 (US).
`
`Designated States (unless otherwise indicated, for every
`kind ofnational protection available): AE, AG, AL, AM,
`Ao, AT, AU, AZ, BA, BB, BG, BH, BN, BR, BW, BY,
`
`BZ, CA, CH, CL, CN, Co, CR, CU, CZ, DE, DK, DM,
`DO, DZ, EC, EE, EG, ES, FI, GB, GD, GE, GH, GM, GT,
`HN, HR, HU, ID, IL, IN, IR, IS, JP, KE, KG, KN, KP, KR,
`KZ, LA, LC, LK, LR, LS, LT, LU, LY, MA, MD, ME,
`MG, MK, MN, MW, MX, MY, MZ, NA, NG, NI, NO, NZ,
`OM, PA, PE, PG, PH, PL, PT, QA, Ro, RS, RU, RW, SA,
`SC, SD, SE, SG, SK, SL, SM, ST, sv, SY, TH, TJ, TM,
`TN, TR, TT, TZ, UA, UG, US, UZ, VC, VN, ZA, ZM,
`ZW.
`
`(84)
`
`Designated States (unless otherwise indicated, for every
`kind of regional protection available): ARIPO (BW, GH,
`GM, KE, LR, LS, MW, MZ, NA, RW, SD, SL, SZ, TZ,
`UG, ZM, ZW), Eurasian (AM, AZ, BY, KG, KZ, RU, TJ,
`TM), European (AL, AT, BE, BG, CH, CY, CZ, DE, DK,
`EE, ES, FI, FR, GB, GR, HR, HU, IE, IS, IT, LT, LU, LV,
`MC, MK, MT, NL, NO, PL, PT, RO, RS, SE, SI, SK, SM,
`TR), OAPl (BF, BJ, CF, CG, CI, CM, GA, GN, GQ, Gw,
`KM, ML, MR, NE, SN, TD, TG).
`Published:
`
`with international search report (Art. 21(3))
`
`before the expiration of the time limit for amending the
`claims and to be republished in the event of receipt of
`amendments (Rule 48.2(h))
`
`(54) Title: PHYSICAL LAYER FRAME FORMAT FOR WLAN
`
`FIG. 7A
`
`700 1
`
`705 V
`
`UHTr
`UHTr UHTr UHTr
`UHTr UHTr
`
`L'STF
`L'LTF
`L'S'G SlGA1
`SIGAZ
`STF
`LTF
`LTF
`SIGB
`UHT'DATA
`J
`J
`J
`J
`J
`J
`J
`J
`J
`J
`
`
`
`
`
`
`
`
`
`706
`7‘10
`712-1
`712-M 714
`702
`704
`708-1 708-2
`7‘16
`
`FIG. 7B
`
`LrSIG
`BPSK
`
`+1
`
`UHT-SIGA’l
`DF'SK Q
`
`UHT-SIGA2
`Q-BF'SK
`
`Q
`
`
`
`(57) Abstract: A first field of a preamble of a data unit is generated to include a first set of one or more information bits that indicate
`a duration of the data unit and is formatted to conform to a first (new) communication protocol and such that the first field allows a
`receiver device that conforms to a second (legacy) communication protocol to determine the duration of the data unit. A second field
`of a preamble of a data unit is generated to include a second set of one or more information bits that indicate to a receiver device that
`conforms to the first (new) communication protocol that the data unit conforms to the first (new) communication protocol. The
`second field is convolutionally coded using a tail biting technique, and the first field and the second field are modulated using a
`modulation scheme specified for a field corresponding to the first field and the second field, respectively, by the second (legacy)
`communication protocol.
`
`
`
`wo2014/183059A1|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
`
`
`
`WO 2014/183059
`
`PCT/US2014/037534
`
`PHYSICAL LAYER FRAME FORMAT FOR WLAN
`
`Cross-References to Related Applications
`
`[0001]
`
`This claims the benefit of US. Provisional Patent Application No. 61/821,947, filed
`
`May 10, 2013, entitled “Physical Layer Frame Format for WLAN,” the disclosure of which is
`
`hereby expressly incorporated herein by reference in its entirety.
`
`[0002]
`
`This application is also related to US. Patent Application No. 13/856,277, filed
`
`April 3, 2013, entitled “Physical Layer Frame Format for WLAN,” the disclosure of Which is
`
`hereby expressly incorporated herein by reference in its entirety.
`
`Field of the Disclosure
`
`[0003]
`
`The present disclosure relates generally to communication networks and, more
`
`particularly, to wireless local area networks that utilize orthogonal frequency division
`
`multiplexing (OFDM).
`
`Background
`
`[0004] When operating in an infrastructure mode, wireless local area networks (WLANs)
`
`typically include an access point (AP) and one or more client stations. WLANs have evolved
`
`rapidly over the past decade. Development of WLAN standards such as the Institute for
`
`Electrical and Electronics Engineers (IEEE) 802.11a, 802.11b, 802.11g, and 802.11n
`
`Standards has improved single-user peak data throughput. For example, the IEEE 802.1 lb
`
`Standard specifies a single-user peak throughput of 11 megabits per second (Mbps), the IEEE
`
`802.1 la and 802.11g Standards specify a single-user peak throughput of 54 Mbps, the IEEE
`
`802.1 1n Standard specifies a single-user peak throughput of 600 Mbps, and the IEEE
`
`802.1 lac Standard specifies a single-user peak throughput in the gigabits per second (Gbps)
`
`range. Future standards promise to provide even greater throughputs, such as throughputs in
`
`the tens of Gbps range.
`
`Sum—mafia
`
`[0005]
`
`In an embodiment, a method for generating a data unit for transmission via a
`
`communication channel, the data unit conforming to a first communication protocol, includes
`
`generating a first field to be included in a preamble of the data unit, wherein the first field
`_ 1 _
`
`
`
`WO 2014/183059
`
`PCT/US2014/037534
`
`includes a first set of one or more information bits that indicate a duration of the data unit, the
`
`first field being formatted such that the first field is decodable by a receiver device that
`
`conforms to a second communication protocol, but does not conform to the first
`
`communication protocol, to determine the duration of the data unit based on the first field.
`
`The method also includes generating a second field to be included in the preamble, wherein
`
`the second field includes a second set of one or more information bits that indicate to a
`
`receiver device that conforms to the first communication protocol that the data unit conforms
`
`to the first communication protocol, and wherein generating the second field includes one or
`
`both of (i) generating the second set of one or more information bits according to an error
`
`detection scheme not specified by the second communication protocol and (ii) generating the
`
`second set of one or more information bits to indicate a mode not supported by the second
`
`communication protocol. The method further includes modulating the first field using a
`
`modulation scheme specified for a field corresponding to the first field by the second
`
`communication protocol. The method fiarther includes convolutionally coding the second
`
`field using a tail biting technique and modulating the convolutionally coded second field
`
`using a modulation scheme specified for a field corresponding to the second field by the
`
`second communication protocol. The method additionally includes generating the preamble
`
`to include at least the first field and the second field, and generating the data unit to include at
`
`least the preamble.
`
`[0006]
`
`In other embodiments,
`
`the method includes any suitable combination of one or
`
`more of the following elements.
`
`[0007]
`
`Convolutionally coding the second field using a tail biting technique comprises
`
`initializing an encoder with one or more last bits of a block of data that includes the second
`
`field,
`
`inputting the block of data that
`
`includes the second field to the encoder and
`
`convolutionally coding the block of data that includes the seocnd field using the initialized
`
`encoder.
`
`[0008]
`
`Generating the second set of one or more information bits according to the error
`
`detection scheme not specified by the second communication protocol comprises generating a
`
`cyclic redundancy check (CRC) for the second field according to a CRC polynomial different
`
`than a CRC polynomial specified for the corresponding field by the second communication
`
`protocol.
`
`[0009]
`
`Generating the second set of one or more information bits according to the error
`
`detection scheme not specified by the second communication protocol comprises generating a
`
`-2-
`
`
`
`WO 2014/183059
`
`PCT/US2014/037534
`
`cyclic redundancy check (CRC) for the second field, including generating a plurality of CRC
`
`bits according to a CRC polynomial specified for the corresponding field by the second
`
`communication protocol, and encrypting one or more bits of the plurality of CRC bits to
`
`generate the CRC for the second field.
`
`[0010]
`
`Generating the second set of one or more information bits according to the error
`
`detection scheme not specified by the second communication protocol comprises generating a
`
`cyclic redundancy check (CRC) for the second field, including generating a plurality of CRC
`
`bits according to a CRC polynomial specified for the corresponding field by the second
`
`communication protocol, selecting a subset of the plurality of CRC bits, the subset to be
`
`utilized for the CRC for the second field; and encrypting one or more bits in the selected
`
`subset of the plurality of CRC bits to generate the CRC for the second field.
`
`[0011]
`
`The second field includes a modulation and coding (MCS) subfield, and wherein
`
`generating the second set of one or more information bits to indicate the mode not supported
`
`by the second communication protocol includes generating the MCS subfield to indicate a
`
`modulation and coding scheme not supported by the second communication protocol.
`
`[0012]
`
`The second field further includes an indication that the data unit conforms to the
`
`first communication protocol.
`
`[0013]
`
`The second communication protocol conforms to the Institute for Electrical and
`
`Electronics Engineers (IEEE) 802.1 lac Standard.
`
`[0014]
`
`The first communication protocol is a communication protocol that supports a
`
`higher throughput than the IEEE 802.1 lac Standard.
`
`[0015]
`
`In another embodiment, an apparatus comprises a network interface configured to
`
`generate a first field to be included in a preamble of the data unit, wherein the first field
`
`includes a first set of one or more information bits that indicate a duration of the data unit, the
`
`first field being formatted such that the first field is decodable by a receiver device that
`
`conforms to a second communication protocol, but does not conform to the first
`
`communication protocol, to determine the duration of the data unit based on the first field.
`
`The network interface is also configured to generate a second field to be included in the
`
`preamble, wherein the second ficld includes a second set of one or more information bits that
`
`indicate to a rcccivcr device that conforms to the first communication protocol that the data
`
`unit conforms to the first communication protocol, and wherein generating the second ficld
`
`includes one or both of (i) generating the second set of one or more information bits
`
`according to an error detection scheme not specified by the second communication protocol
`
`-3-
`
`
`
`WO 2014/183059
`
`PCT/US2014/037534
`
`and (ii) generating the second set of one or more information bits to indicate a mode not
`
`supported by the second communication protocol.
`
`The network interface is further
`
`configured to modulate the first field using a modulation scheme specified for a field
`
`corresponding to the first field by the second communication protocol. The network interface
`
`is fithher configured to convolutionally code the second field using a tail biting technique and
`
`modulate the convolutionally coded second field using a modulation scheme specified for a
`
`field corresponding to the second field by the second communication protocol. The network
`
`interface is additionally configured to generate the preamble to include at least the first field
`
`and the second field, and generate the data unit to include at least the preamble.
`
`[0016]
`
`In other embodiments, the apparatus includes any suitable combination of one or
`
`more of the following features.
`
`[0017]
`
`The network interface is configured to initialize an encoder with one or more last
`
`bits ofa block of data that includes the second field, input the block of data that includes the
`
`second field to the encoder, and convolutionally code the block of data that includes the
`
`second field using the initialized encoder.
`
`[0018]
`
`The network interface is configured to generate the second set of one or more
`
`information bits according to the error detection scheme not specified by the second
`
`communication protocol at least by generating a cyclic redundancy check (CRC) for the
`
`second field according to a CRC polynomial different than a CRC polynomial specified for
`
`the corresponding field by the second communication protocol.
`
`[0019]
`
`The network interface is configured to generate the second set of one or more
`
`information bits according to the error detection scheme not specified by the second
`
`communication protocol at least by generating a cyclic redundancy check (CRC) for the
`
`second field, including generating a plurality of CRC bits according to a CRC polynomial
`
`specified for the corresponding field by the second communication protocol, and encrypting
`
`one or more bits of the plurality of CRC bits to generate the CRC for the second field.
`
`[0020]
`
`The network interface is configured to generate the second set of one or more
`
`information bits according to the error detection scheme not specified by the second
`
`communication protocol at least by generating a cyclic redundancy check (CRC) for the
`
`second field, including generating a plurality of CRC bits according to a CRC polynomial
`
`specified for the corresponding field in the second communication protocol, selecting a
`
`subset of the plurality of CRC. the subset to be utilized for the CRC for the second field; and
`
`-4-
`
`
`
`WO 2014/183059
`
`PCT/US2014/037534
`
`encrypting one or more bits in the selected subset of the plurality of C RC bits to generate the
`
`CRC for the second field.
`
`[0021]
`
`The second field includes a modulation and coding (MCS) subfield.
`
`[0022]
`
`The network interface is configured to generate the second set of one or more
`
`information bits to indicate the mode not supported by the second communication protocol at
`
`least by generating the MCS subfield to indicate a modulation and coding scheme not
`
`supported by the second communication protocol.
`
`[0023]
`
`Thc nctwork intcrfacc is furthcr configurcd to includc, in thc sccond ficld, an
`
`indication that thc data unit conforms to thc first communication protocol.
`
`[0024]
`
`The second communication protocol conforms to the Institute for Electrical and
`
`Electronics Engineers (IEEE) 802.1 lac Standard.
`
`[0025]
`
`Thc first communication protocol is a communication protocol that supports a
`
`highcr throughput than the IEEE 802.1 lac Standard.
`
`[0026]
`
`In yet another embodiment, a method includes receiving a data unit, wherein the
`
`data unit conforms to a first communication protocol or to a second communication protocol,
`
`and decoding, using a tail biting technique, a field of a preamble of the data unit, including
`
`decoding a received cyclic redundancy check (CRC) included in the field. The method also
`
`includes generating, based on the field, a first CRC using a first CRC generation scheme, the
`
`first CRC generation scheme specified for the first field by the first communication protocol.
`
`The method filrther includes generating, based on the field, a second CRC using a second
`
`CRC generation scheme, the second CRC generation scheme specified for the field by the
`
`second communication protocol. The method fithher still includes comparing (i) the first
`
`generated CRC and (ii) the second generated CRC to the received CRC. The method
`
`additionally includes determining that the data unit conforms to the first communication
`
`protocol When the first generated CRC matches the received CRC, and determining that the
`
`data unit conforms to the second communication protocol When the second generated CRC
`
`matches the received CRC.
`
`[0027]
`
`In other embodiments, the method includes any suitable combination of one or
`
`more ofthe following elements.
`
`
`
`WO 2014/183059
`
`PCT/US2014/037534
`
`[0028]
`
`Decoding, using a tail biting technique, comprises searching through a plurality of
`
`possible trellis paths with the same initial and ending state and choosing a trellis path of the
`
`plurality of trellis paths with the lowest cost or lowest metric.
`
`[0029]
`
`Generating the first CRC comprises generating the first CRC according to a first
`
`CRC polynomial, the first CRC polynomial specified for the field by the first communication
`
`protocol.
`
`[0030]
`
`Generating the second CRC comprises generating the second CRC according to a
`
`second CRC polynomial, the second CRC polynomial specified for the field by the second
`
`communication protocol, wherein the second CRC polynomial is different than the first CRC
`
`polynomial.
`
`[0031]
`
`Generating the first CRC comprises generating the first CRC according to a first
`
`CRC polynomial, the first CRC polynomial specified for the field by the first communication
`
`protocol.
`
`[0032]
`
`Generating the second CRC comprises generating a plurality of CRC bits according
`
`to the first CRC polynomial, and encrypting one or more bits of the plurality of CRC bits to
`
`generate the second CRC.
`
`[0033]
`
`Generating the second CRC comprises generating a plurality of CRC bits according
`
`to the first CRC polynomial, selecting a subset of the plurality of CRC bits, the subset to be
`
`utilized for the CRC for the second CRC; and encrypting one or more bits in the selected
`
`subset of the plurality of CRC bits to generate the second CRC.
`
`[0034]
`
`In still another embodiment, an apparatus comprises a network interface configured
`
`to receive a data unit, wherein the data unit conforms to a first communication protocol or a
`
`second communication protocol, and decode, using a tail biting technique, a field of a
`
`preamble of the data unit, including decoding a received cyclic redundancy check (CRC)
`
`included in the field. The network interface is also configured to generate, based on the field,
`
`a first CRC using a first CRC generation scheme, the first CRC generation scheme specified
`
`for the first field by the first communication protocol, and generate, based on the field, a
`
`second CRC using a second CRC generation scheme, the second CRC generation scheme
`
`specified for the field by the second communication protocol. The network interface is
`
`further configured to compare the first generated CRC and the second generated CRC to the
`
`received CRC. The network interface is additionally configured to determine that the data
`
`unit conforms to the first communication protocol when the first generated CRC matches the
`
`
`
`WO 2014/183059
`
`PCT/US2014/037534
`
`received CRC , and determine that the data unit conforms to the second communication
`
`protocol when the second generated CRC matches the received CRC.
`
`[0035]
`
`In other embodiments, the apparatus includes any suitable combination of one or
`
`more of the following fcaturcs.
`
`[0036]
`
`The network interface is configured to generate the first CRC the first CRC
`
`according to a first CRC polynomial, the first CRC polynomial specified for the field by the
`
`first communication protocol.
`
`[0037]
`
`The network interface is configured to search through a plurality of possible trellis
`
`paths with the same initial and ending state and choose a trellis path of the plurality of trellis
`
`paths with the lowest cost or lowest metric.
`
`[0038]
`
`Generate the second CRC according to a second CRC polynomial, the second CRC
`
`polynomial specified for the field by the second communication protocol, wherein the second
`
`CRC polynomial is different than the first CRC polynomial.
`
`[0039]
`
`Generate the second CRC at least by generating a plurality of CRC bits according
`
`to the first CRC polynomial, and encrypting one or more bits of the plurality of CRC bits to
`
`generate the second CRC.
`
`[0040]
`
`The network interface is configured to generate the first CRC according to a first
`
`CRC polynomial, the first CRC polynomial specified for the field by the first communication
`
`protocol.
`
`[0041]
`
`Generate the second CRC at least by generating a plurality of CRC bits according
`
`to the first CRC polynomial, selecting a subset of the plurality of CRC bits, the subset to be
`
`utilized for the CRC for the second CRC; and encrypting one or more bits in the selected
`
`subset of the plurality of CRC bits to generate the second CRC.
`
`[0042]
`
`In still another embodiment, a method for generating a data unit for transmission
`
`via a communication channel, the data unit conforming to a first communication protocol,
`
`includes generating a preamble of the data unit, wherein the preamble includes a first field
`
`having a plurality of orthogonal frequency division multiplexing (OFDM) symbols, including
`
`at least (i) a first OFDM symbol, (i) a second OFDM symbol, and (iii) a third OFDM symbol.
`
`The first OFDM symbol is convolutionally coded using a tail biting technique, and is
`
`formatted such that the first OFDM symbol is decodable by a receiver device that conforms
`
`to a second communication protocol, but does not conform to the first communication
`
`protocol, to determine that the data unit conforms to a third communication protocol. The
`
`second OFDM symbol is formatted such that the first OFDM symbol and the second OFDM
`
`-7-
`
`
`
`WO 2014/183059
`
`PCT/US2014/037534
`
`symbol are decodable by a receiver device that conforms to a fourth communication protocol,
`
`but does not conform to the first communication protocol, to determine that the data unit
`
`conforms to the third communication protocol. The third OFDM symbol is formatted such
`
`that a receiver device that conforms to the first communication protocol can determine that
`
`the data unit conforms to the first communication protocol. The network interface is also
`
`configured to generate the data unit to include at least the preamble.
`
`[0043]
`
`In other embodiments, the method includes any combination of one or more of the
`
`following elements.
`
`[0044] A second field of the preamble substantially conforms to the third communication
`
`protocol, and wherein the second field includes a rate and a length subfield that indicate the
`
`duration of the data unit.
`
`[0045]
`
`The first OFDM symbol is modulated using the same modulation as the second
`
`OFDM symbol, wherein the modulation is different than the modulation specified for the
`
`corresponding OFDM symbols by the second communication protocol.
`
`[0046]
`
`The second communication protocol conforms to the Institute for Electrical and
`
`Electronics Engineers (IEEE) 802.1 1n Standard.
`
`[0047]
`
`The third communication protocol conforms to the IEEE 802.11a Standard.
`
`[0048]
`
`The fourth communication protocol conforms to the IEEE 802.1 lac Standard.
`
`[0049]
`
`The first communication protocol is a communication protocol that supports a
`
`higher throughput than the IEEE 802.1 lac Standard.
`
`[0050]
`
`In still another embodiment, an apparatus comprises a network interface configured
`
`to generate a preamble of the data unit, wherein the preamble includes a first field having a
`
`plurality of orthogonal frequency division multiplexing (OFDM) symbols, including at least
`
`(i) a first OFDM symbol, (i) a second OFDM symbol, and (iii) a third OFDM symbol. The
`
`first OFDM symbol is convolutionally coded using a tail biting technique, and is formatted
`
`such that the first OFDM symbol is decodable by a receiver device that conforms to a second
`
`communication protocol, but does not conform to the first communication protocol, to
`
`determine that the data unit conforms to a third communication protocol. The second OFDM
`
`symbol is formatted such that the first OFDM symbol and the second OFDM symbol are
`
`decodable by a receiver device that conforms to a fourth communication protocol, but does
`
`not conform to the first communication protocol, to determine that the data unit conforms to
`
`-8-
`
`
`
`WO 2014/183059
`
`PCT/US2014/037534
`
`the third communication protocol. The third OFDM symbol is formatted such that a receiver
`
`deVice that conforms to the first communication protocol can determine that the data unit
`
`conforms to the first communication protocol. The network interface is also configured to
`
`generate the data unit to include at least the preamble.
`
`[0051]
`
`In other embodiments, the apparatus includes any combination of onc or more of
`
`thc following features.
`
`[0052]
`
`The network interface is fiarther configured to generate a second field of the
`
`preamble, wherein the second field (i) substantially conforms to the third communication
`
`protocol, and (ii) includes a rate and a length subfield that indicate the duration of the data
`
`unit.
`
`[0053]
`
`The network interface is configured to modulate the first OFDM symbol using the
`
`same modulation as the second OFDM symbol, wherein the modulation is different than the
`
`modulation specified for the corresponding OFDM symbols by the second communication
`
`protocol .
`
`Brief Description of the Drawings
`
`[0054]
`
`Fig. l is a block diagram of an example wireless local area network (WLAN) 10,
`
`according to an embodiment.
`
`[0055]
`
`Figs. 2A and 2B are diagrams of a prior art data unit format.
`
`[0056]
`
`Fig. 3 is a diagram of another prior art data unit format.
`
`[0057]
`
`Fig. 4 is a diagram of another prior art data unit format.
`
`[0058]
`
`[0059]
`
`Fig. 5 is a diagram of an example data unit format, according to an embodiment.
`
`[0060]
`
`Fig. 6A arc diagrams of modulation uscd to modulatc symbols in a prior art data
`
`unit.
`
`[0061]
`
`Fig. 6B are diagrams of modulation used to modulate symbols in an example data
`
`unit, according to an embodiment.
`
`[0062]
`
`Fig. 7A is a diagram of an example data unit format, according to an embodiment.
`
`[0063]
`
`Fig. 7B shows diagrams of modulation used to modulate symbols in the data unit
`
`depicted in Fig. 7A, according to an embodiment.
`
`
`
`WO 2014/183059
`
`PCT/US2014/037534
`
`[0064]
`
`Figs. 8A-8G are diagrams of example bit allocations for a signal field, according to
`
`an embodiment.
`
`[0065]
`
`Figs 9A-9C are diagrams depicting several example cyclic redundancy check
`
`(CRC) gcncration schcmcs, according to several embodiments.
`
`[0066]
`
`Fig. 10 is a block diagram depicting a detection scheme for detecting whether a
`
`data unit conforms to a first communication protocol or to a second communication protocol,
`
`according to an embodiment.
`
`[0067]
`
`Fig. ll is a block diagram depicting anothcr dctcction scheme for detecting whether
`
`a data unit conforms to a first communication protocol or to a second communication
`
`protocol, according to an embodiment.
`
`[0068]
`
`Fig. 12 is a block diagram depicting yet another detection scheme for detecting
`
`Whether a data unit conforms to a first communication protocol or to a second communication
`
`protocol, according to an embodiment.
`
`[0069]
`
`Fig. 13A is a diagram of an cxamplc data unit format, according to an embodiment.
`
`[0070]
`
`Fig. 13B are diagrams of modulation used to modulate symbols in the data unit
`
`depicted in Fig. 13A, according to an embodiment.
`
`[0071]
`
`Fig. 14A is a diagram of an cxamplc data unit format, according to an embodiment.
`
`[0072]
`
`Fig. 14B are diagrams of modulation used to modulate symbols in the data unit
`
`depicted in Fig. 14A, according to an embodiment.
`
`[0073]
`
`Fig. 15A is a block diagram of an example transmitter according to an embodiment.
`
`[0074]
`
`Fig. 15B is a block diagram of a receiver according to an embodiment.
`
`[0075]
`
`Fig. 16 is a diagram of a method for generating a data unit, according to an
`
`embodiment.
`
`[0076]
`
`Fig. 17 is a diagram of a method for detecting whether a data unit conforms to a
`
`first communication protocol or to a second communication protocol, according to an
`
`embodiment.
`
`[0077]
`
`Fig. 18 is a diagram of a method for generating a data unit, according to an
`
`embodiment.
`
`[0078]
`
`Fig. 19A is a diagram of an example data unit format, according to an embodiment.
`
`-10-
`
`
`
`WO 2014/183059
`
`PCT/US2014/037534
`
`[0079]
`
`Fig. 19B is a diagram of an example data unit format, according to an embodiment.
`
`[0080]
`
`Fig. 20A is a diagram of an example data unit format, according to an embodiment.
`
`[0081]
`
`Fig. 20B is a diagram of an example data unit format, according to an embodiment.
`
`[0082]
`
`Fig. 21A is a diagram of an example data unit format, according to an embodiment.
`
`[0083]
`
`Fig. 21B is a diagram of an example data unit format, according to an embodiment.
`
`[0084]
`
`Fig. 22A is a diagram of an example data unit format, according to an embodiment.
`
`[0085]
`
`Fig. 22B is a diagram of an example data unit format, according to an embodiment.
`
`Detailed Description
`
`[0086]
`
`In embodiments described below, a wireless network device such as an access point
`
`(AP) of a wireless local area network (WLAN) transmits data streams to one or more client
`
`stations. The AP is configured to operate with client stations according to at least a first
`
`communication protocol. The first communication protocol, according to some
`
`embodiments, is referred herein as “ultra high throughput” or “UHT” communication
`
`protocol. In some embodiments, different client stations in the vicinity of the AP are
`
`configured to operate according to one or more other communication protocols which define
`
`operation in the same frequency band as the UHT communication protocol but with generally
`
`lower data throughputs. The lower data throughput communication protocols (e.g., IEEE
`
`802.1 la, IEEE 802.1 In, and/or IEEE 802.1 lac) are collectively referred herein as “legacy”
`
`communication protocols. When the AP transmits a data unit according to the UHT
`
`communication protocol, a preamble of the data is formatted such that a client station that
`
`operates according to a legacy protocol, and not the UHT communication protocol, is able to
`
`determine certain information regarding the data unit, such as a duration of the data unit,
`
`and/or that the data unit does not conform to the second protocol. Additionally, a preamble
`
`of the data unit is formatted such that a client station that operates according to the UHT
`
`protocol is able to determine the data unit conforms to the UHT communication protocol.
`
`Similarly, a client station configured to operate according to the UHT communication
`
`protocol also transmits data units such as described above.
`
`[0087]
`
`In at least somc cmbodimcnts, data units formattcd such as dcscribcd abovc arc
`
`useful, for example, with an AP that is configured to opcratc with client stations according to
`
`-11-
`
`
`
`WO 2014/183059
`
`PCT/US2014/037534
`
`a plurality of different communication protocols and/or with WLANs in which a plurality of
`
`client stations operate according to a plurality of different communication protocols.
`
`Continuing with the example above, a communication device configured to operate according
`
`to both the UHT communication protocol and a legacy communication protocol is able to
`
`determine that the data unit is formatted according to the UHT communication protocol and
`
`not the legacy communication protocol. Similarly, a communication device configured to
`
`operate according to a legacy communication protocol but not the UHT communication
`
`protocol is able to determine that the data unit is not formatted according to the legacy
`
`communication protocol and/or determine a duration of the data unit.
`
`[0088]
`
`Fig. 1 is a block diagram of an example wireless local area network (WLAN) 10,
`
`according to an embodiment. An AP 14 includes a host processor 15 coupled to a network
`
`interface 16. The network interface 16 includes a medium access control (MAC) processing
`
`unit 18 and a physical layer (PHY) processing unit 20. The PHY processing unit 20 includes
`
`a plurality oftransceivers 21, and the transceivers 21 are coupled to a plurality of antennas
`
`24. Although three transceivers 21 and three antennas 24 are illustrated in Fig. 1, the AP 14
`
`includes other suitable numbers (e.g., 1, 2, 4, 5, etc.) of transceivers 21 and antennas 24 in
`
`other embodiments. In one embodiment, the MAC processing unit 18 and the PHY
`
`processing unit 20 are configured to operate according to a first communication protocol
`
`(e. g., UHT communication protocol). In another embodiment, the MAC processing unit 18
`
`and the PHY processing unit 20 are also configured to operate according to a second
`
`communication protocol (e. g., IEEE 802.1 lac Standard). In yet another embodiment, the
`
`MAC processing unit 18 and the PHY processing unit 20 are additio